Challenge file: Download.
In fact, this is my first attempt to recover USB traffic from a PCAP file.
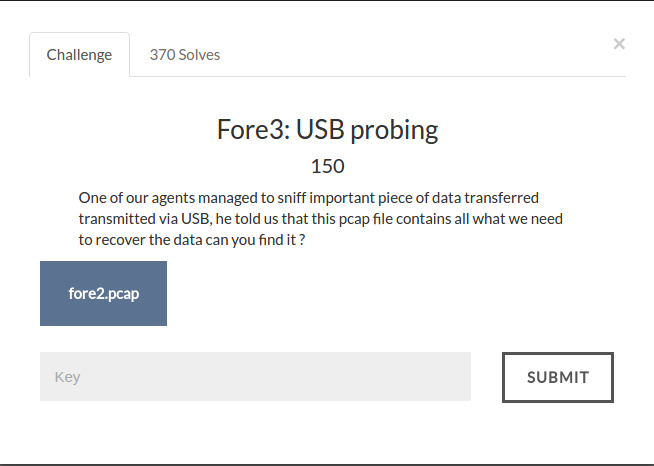
The initial 4 packets had the information of the devices involved in the traffic. Using the Product ID and Vendor ID I did some research here to get the device details. It is a flash drive.
In the following paragraphs I will try to explain my approach to solve this problem but if you just want to see the solution please check the last 2 paragraphs.
Wireshark doesn’t have an easy option to view the transferred files using USB protocol, on the contrary it’s easy to extract or view transferred files in TCP (using TCP stream).
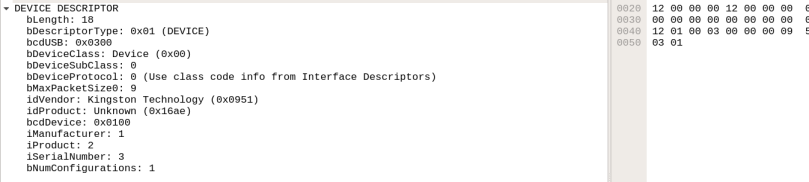
I made a simple test to understand how a simple file is transferred via USB protocol. I plugged in a USB device and transferred a text file ( with contents “findme”*1000). Of course, wireshark was listening to the usb interface in the background. To capture the USB traffic you must load the USB kernel module (check here).
$ sudo modprobe usbmon
Most of the packet’s sizes were less than 100 bytes and the transferred text file was found in a packet having a length greater than 1000 bytes, check the URB_BULK out.
So as a conclusion check for the packets having size greater than 1000 bytes with flags URB_BULK out/in. Also I found the file names that were present inside the flash drive.
Let’s repeat the same steps to find what was transferred. Load up the challenge file and try to find the packets having length greater than 1000 bytes. Go down a bit and bingo, you can find the PNG image’s header! 😉
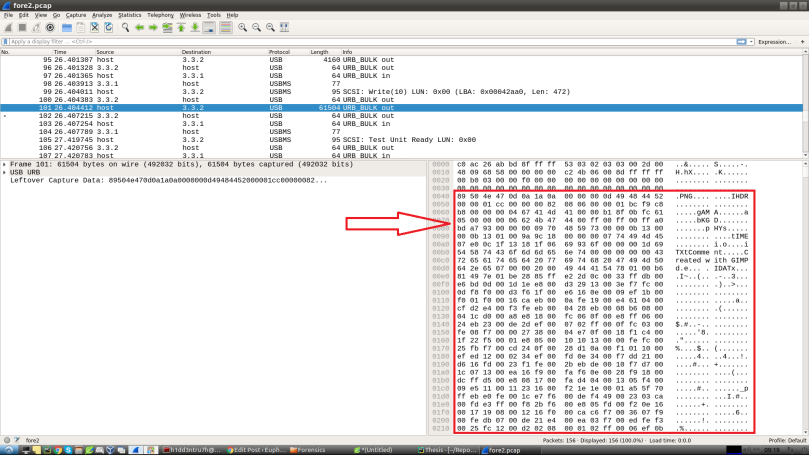
Select the stream and press Ctrl + h or you can use File->Export Packet Bytes. Open the saved file in a image viewer and you see the flag!!
