From the given PCAP file you must have noticed the traffic from OSCP, HTTP, FTP, SMTP and TLS protocol. TLS has the actual flag, FTP has the private key to decrypt the TLS traffic and SMTP has the clue that will help us in filtering the traffic of interest i.e the right TLS packets. You can ignore the rest.
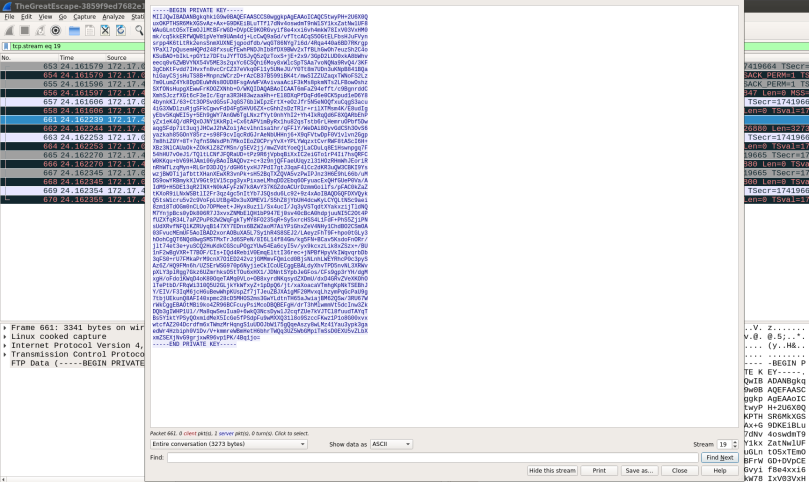
The first task is to retrieve the private key file from the FTP traffic. Use the filter “ftp-data” in wireshark. Do a TCP stream, you can see the transferred private key. Save that as a text file ( private_key.txt).
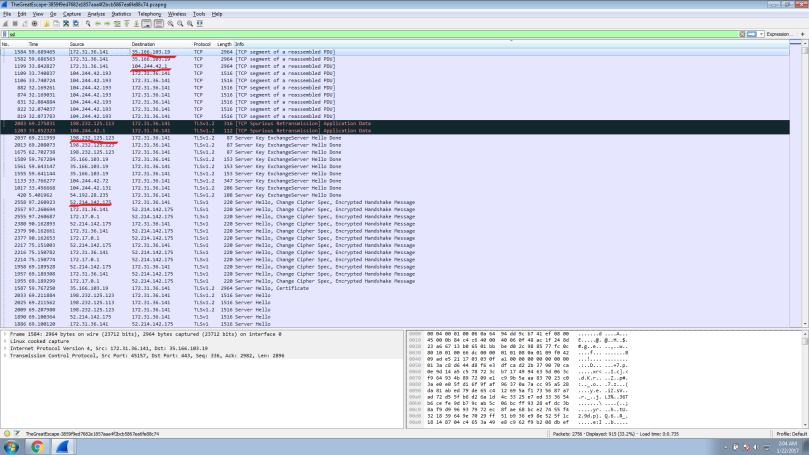
We have the private key and all we have to do is to use it and decrypt the TLS packets. Use the filter “ssl” to see the encrypted traffic.
We have 4+ HTTP servers involved and the important task is to find the right one that has the flag. But how? The answer is in the hint transmitted in the email (SMTP traffic). Use the filter “smtp” and read the contents of the email. You can see the sender informing about moving the code from Swiss Secure Cloud to tge.teaser.insomnihack.ch. May be the flag was transmitted here!
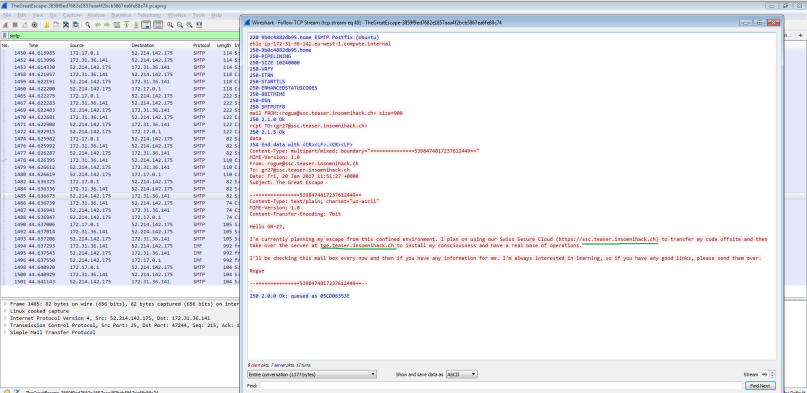
The two addresses found in the email points to 52.214.142.175 : 443. So this might be the right IP address we are looking for.

To confirm, see if there is any traffic originating from 52.214.142.175 in the PCAP file. You will see the encrypted traffic. Let’s use all the information we gathered from the SMTP protocol ( IP : 52.214.142.175, PORT : 443) and FTP (the private key) to decrypt the SSL traffic.
Go to Edit->Preferences->Protocols->SSL. In the RSA key list add all the information we got. The protocol should be http as the port no for 52.214.142.175 is 443 ( default for https).
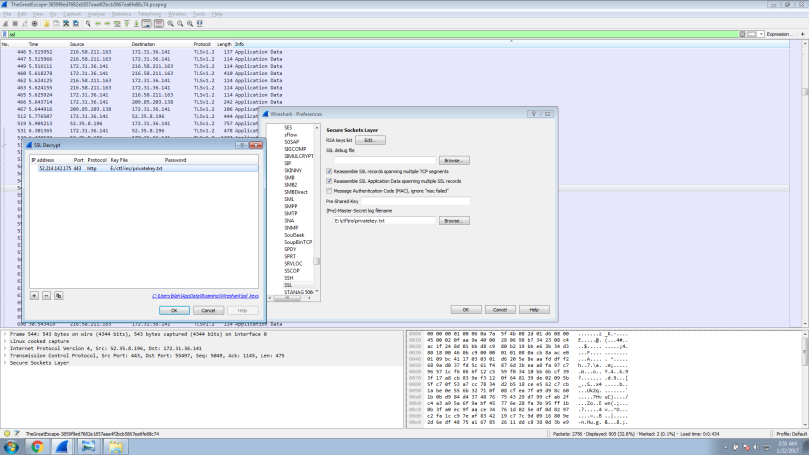
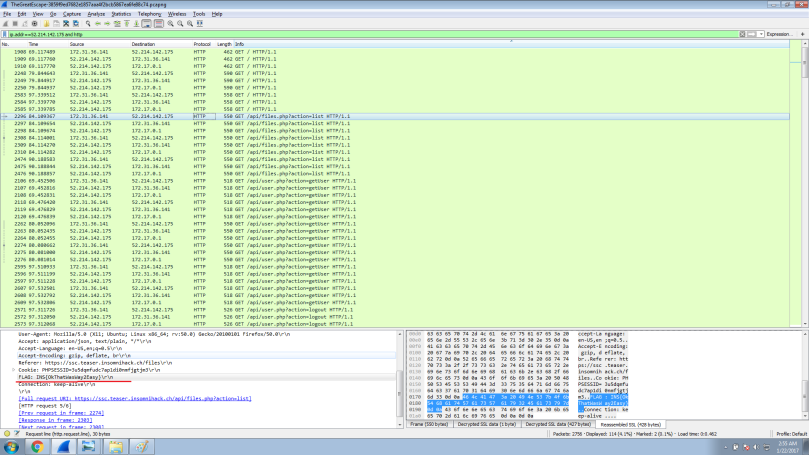
Use the filter “ip.addr==52.214.142.175 and http”. You can see the deciphered traffic.
I was searching for the flag inside the transferred files ( File -> Export-> HTTP objects) but it was not there, after a while I found it in the HTTP header.