I was not able to participate in the contest properly, but I was able to solve at least 2 challenges. This time the challenges were interesting compared to the previous edition. Really I missed those challenges! Here is my writeup, They gave a ext3 filesystem disk image and we have to recover the deleted file. The size of the disk image is roughly around 2MB.
➜ SU-CTF [0] file disk-image disk-image: Linux rev 1.0 ext3 filesystem data, UUID=bc6c2b24-106a-4570-bc4f-ae09abbd7a88
Disk recovery tools like foremost,photorec etc failed to recover the deleted file. Then I tried to finish the challenge in an easier way by grep’ng for “flag”,
➜ SU-CTF [0] strings disk-image| grep "flag" flag flag flag your flag is:
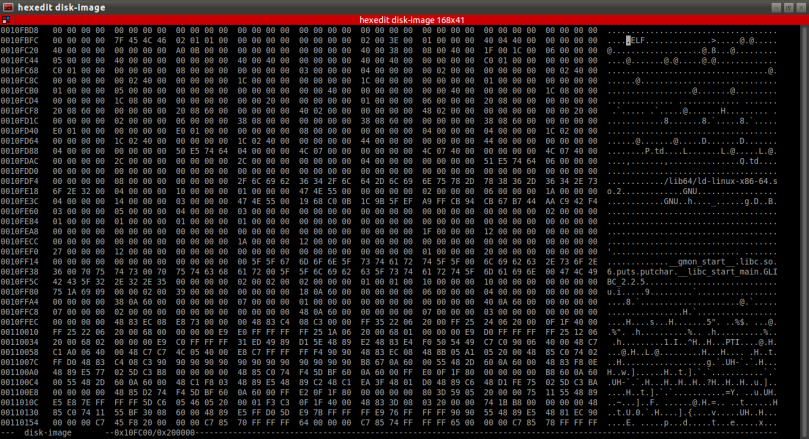
Okay! we can see the word “flag” in the stdout, but where did the flag go?. I went through the strings stdout and found the stack layout and libraries like gcc, __libc_start_main, call_gmon_start etc. So the deleted file is an executable file? Will confirm it. I opened the disk image in a hex editor for finding file signatures. And there was an 64 bit ELF file found in the image at offset 0x10FC00.
Now we will extract the ELF file using dd,
➜ SU-CTF [0] dd if=disk-image bs=1 skip=1113088 of=flag.out 984064+0 records in 984064+0 records out 984064 bytes (984 kB) copied, 1.65457 s, 595 kB/s
And when I run the ELF file, I got the flag to be: de6838252f95d3b9e803b28df33b4baa,
➜ SU-CTF [0] ./flag.out your flag is: de6838252f95d3b9e803b28df33b4baa%